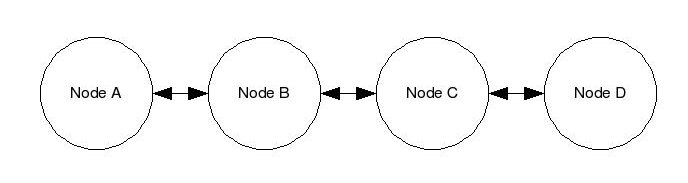
| Node |
MAC Address |
IP Address |
| A |
AA:AA:AA:AA:AA:AA |
192.168.0.1 |
| B |
BB:BB:BB:BB:BB:BB |
192.168.0.2 |
| C |
CC:CC:CC:CC:CC:CC |
192.168.0.3 |
| D |
DD:DD:DD:DD:DD:DD |
192.168.0.4 |